🔒 Auto Logout Settings
The Auto Logout feature in CLH Web Security Lite enhances website security by automatically logging out inactive users. This helps prevent unauthorized access if a user forgets to log out, reducing the risk of session hijacking and other security threats.
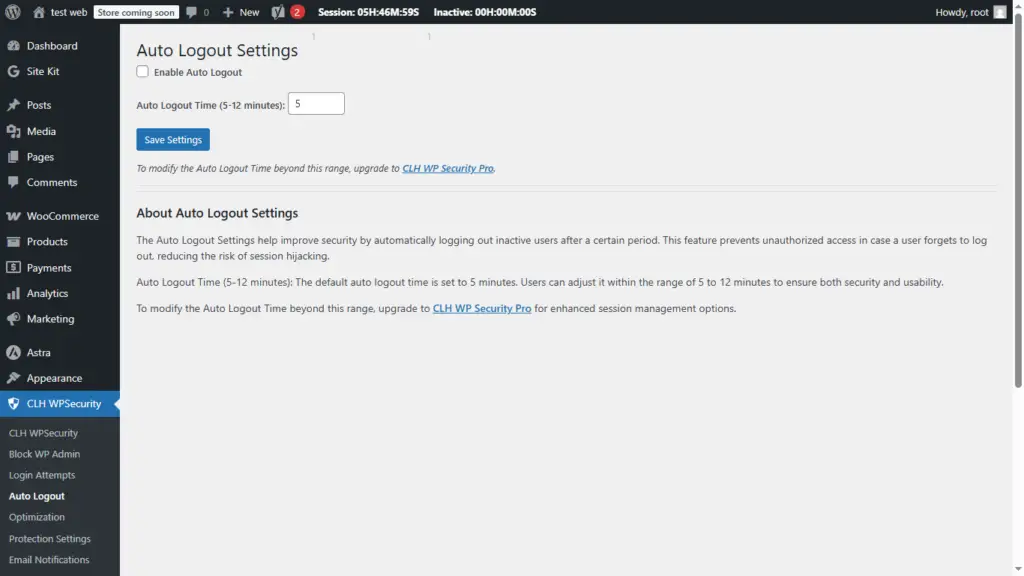
🔧 Configuring Auto Logout Time
By default, WordPress does not log out inactive users, which can lead to security risks. CLH Web Security Lite allows you to enforce an Auto Logout Timer to maintain security.
✅ Auto Logout Enabled: ✅
✅ Auto Logout Time: 5 minutes (Range: 5 to 12 minutes)
🔹 Want to set a custom logout time beyond this range? Upgrade to CLH Web Security Pro.
🔹 Why Auto Logout is Important?
1. Prevents Unauthorized Access
If a user forgets to log out, their session remains active. Auto Logout ensures that inactive users are logged out, preventing unauthorized access.
2. Reduces the Risk of Session Hijacking
Hackers can hijack active sessions to gain control of a user’s account. Automatic logout reduces this risk by limiting session duration.
3. Improves Website Security
Auto Logout helps maintain security compliance, especially for websites handling sensitive user data or admin-level access.
4. Enhances Performance & Server Efficiency
By reducing long-running sessions, Auto Logout optimizes server resources, improving overall site performance.
🔐 Unlock Advanced Session Management with CLH Web Security Pro
Upgrading to CLH Web Security Pro allows you to:
✅ Set Auto Logout Time beyond the 5-12 minute range
✅ Enable custom logout warnings before auto logout
✅ Manage session timeout settings for specific user roles
Conclusion
Enforcing Auto Logout is a crucial security measure to prevent unauthorized access and enhance session management. With CLH Web Security Lite, you can set an auto logout timer between 5 to 12 minutes. For greater flexibility and advanced control, upgrade to CLH Web Security Pro today! 🚀
Cybersecurity Disclaimer
This content is for educational and ethical purposes only. We do not promote or condone illegal hacking, unauthorized access, or malicious activities.
By using this content, you agree to follow legal and ethical guidelines. Misuse may lead to legal penalties under the IT Act & BNS.
View Full Legal DisclaimerSupport Independent Content
Help us continue providing high-quality educational resources by making a donation. Every contribution makes a difference!





